In versions of OS X prior to El Capitan, the ability to edit files in /System and other system locations was restricted to root. Now, in OS X El Capitan, Rootless means that there is no longer the ability for root to edit these files. This means that El Capitan Rootless blocking Installer.app can happen with standard installer packages, because even though a password has been entered into the standard OS X administrator privileges dialog box, the ability to write files to locations that the system may read from has been prevented.
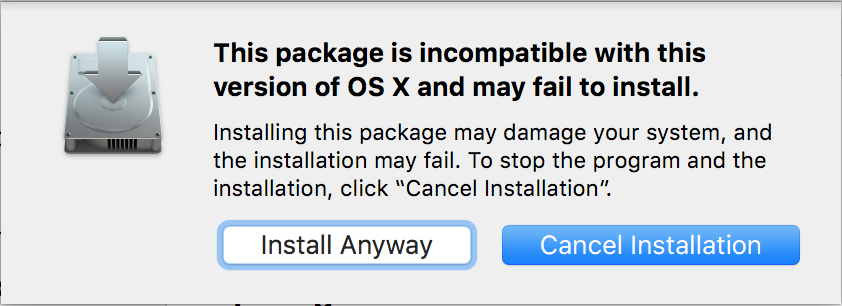
The following error message is shown if you attempt to install a package in 10.11 with Rootless enabled:
This package is is incompatible with this version of OS X and may fail to install.
Installing this package may damage your system, and the installation may fail. To stop the program and the installation, click
Cancel Installation.Install Anyway – Continue Installation
Certain packages created for Installer.app may have been designed for an older version of OS X that allows writing files into these protected locations. These packages can't be installed in OS X El Capitan with Rootless enabled, because the write action would be prevented. There are three possible solutions to this problem:
Request an updated installer from the developer of the software
The software developer can update the installer to not need to write certain files as part of the installer package. This will probably mean that the software itself needs to be updated, to either look for files in a different location or to workaround the prohibition and provide a means to do the same function without needing the certain custom system files. In the worst case with system utilities, this may result in a reduction of functionality.
Disable OS X El Capitan Rootless and permit write actions to System Integrity Protection locations
This is not an ideal solution as this reduces the security of the system, however in some cases this is the only option, where the software has not been updated or cannot be updated to be compatible with the new security restrictions.
To disable System Integrity Protection, you can do the following:
- Boot into the Recovery HD by restarting whilst holding ⌘R.
- Open Terminal (from the Utilities menu).
- Run the following command in Terminal:
csrutil disable - Restart.
This will allow the user to make modifications to protected locations and thus allow Installer.app to make modifications on behalf of the user. System Integrity Protection can be disabled once Installer.app has finished making the modifications, however this may cause problems if write access to containing folders is required in the future by the app.
Extract the app from the package yourself
In cases where the software or files that needs to be installed in a protected location is supplementary to the functionality of the software, you may be able to extract the core files from the package and install it yourself in a different location. A good app for doing this is Pacifist, which allows you to open packages (and meta-packages) and extract individual files and folders to custom locations. Whilst the entire functionality of the program may be reduced by this procedure and crashes may ensue, it is possible to work around System Integrity Protection without the need to disable it.
the package is trying to install content to the system volume. contact the software manufacturer for assistance
I experienced something similar with McAfee recently. Suddenly a tidal wave of attacks and data breaches. This was only noted when I had several "Reset Password" messages in two days. Apparently there was no help/advice from McAfee , Just a message stating NO FIREWALL PROTECTION, as NOT compatible with new OS BIG SUR. Surely some sort of warning should be given prior to installation of new OS. Having only re-subscribed in November 2020 have now NO TRUST or FAITH in McAfee protection any more. Where to go now?